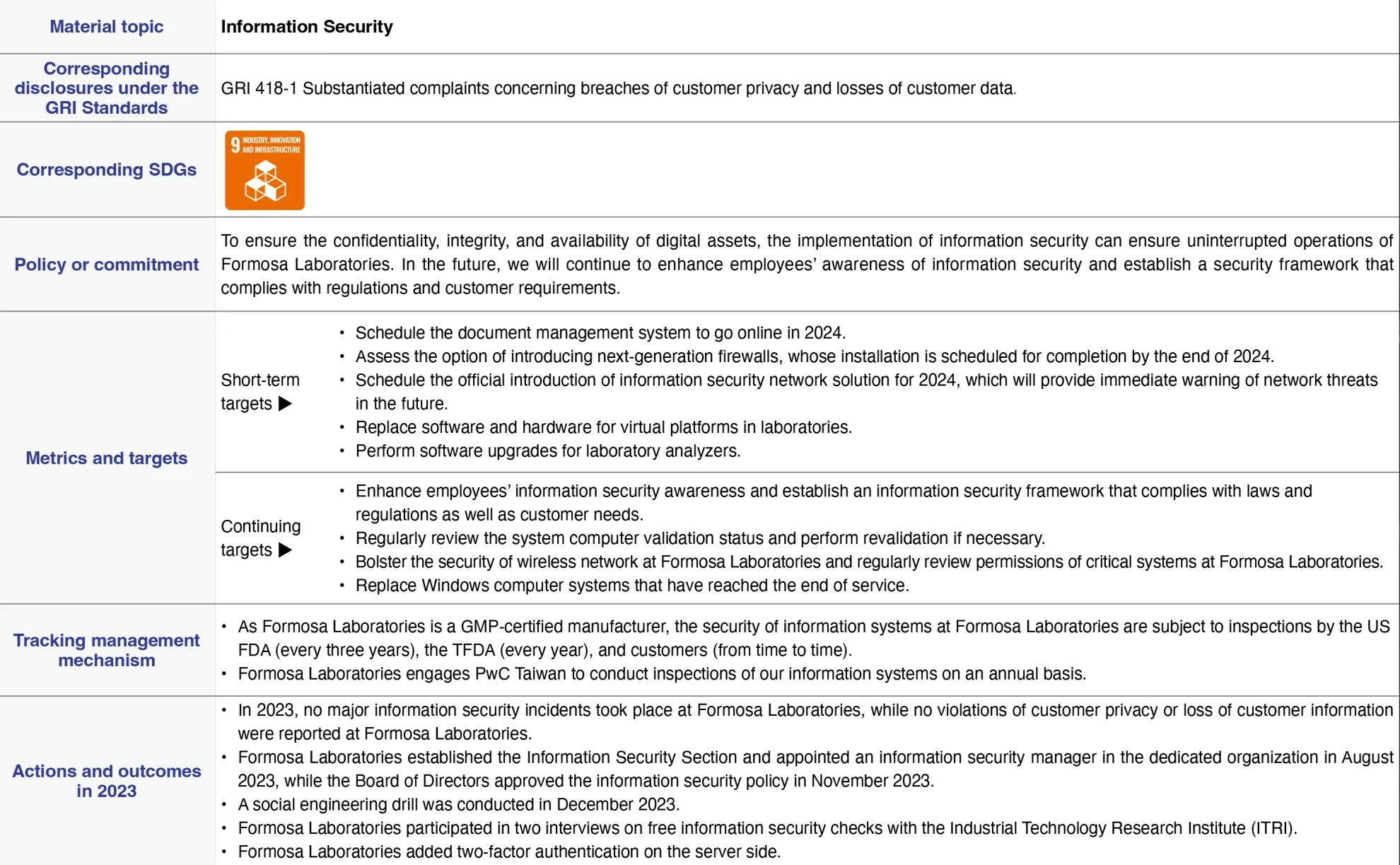
Management of material topic “information security” at Formosa Laboratories in 2023
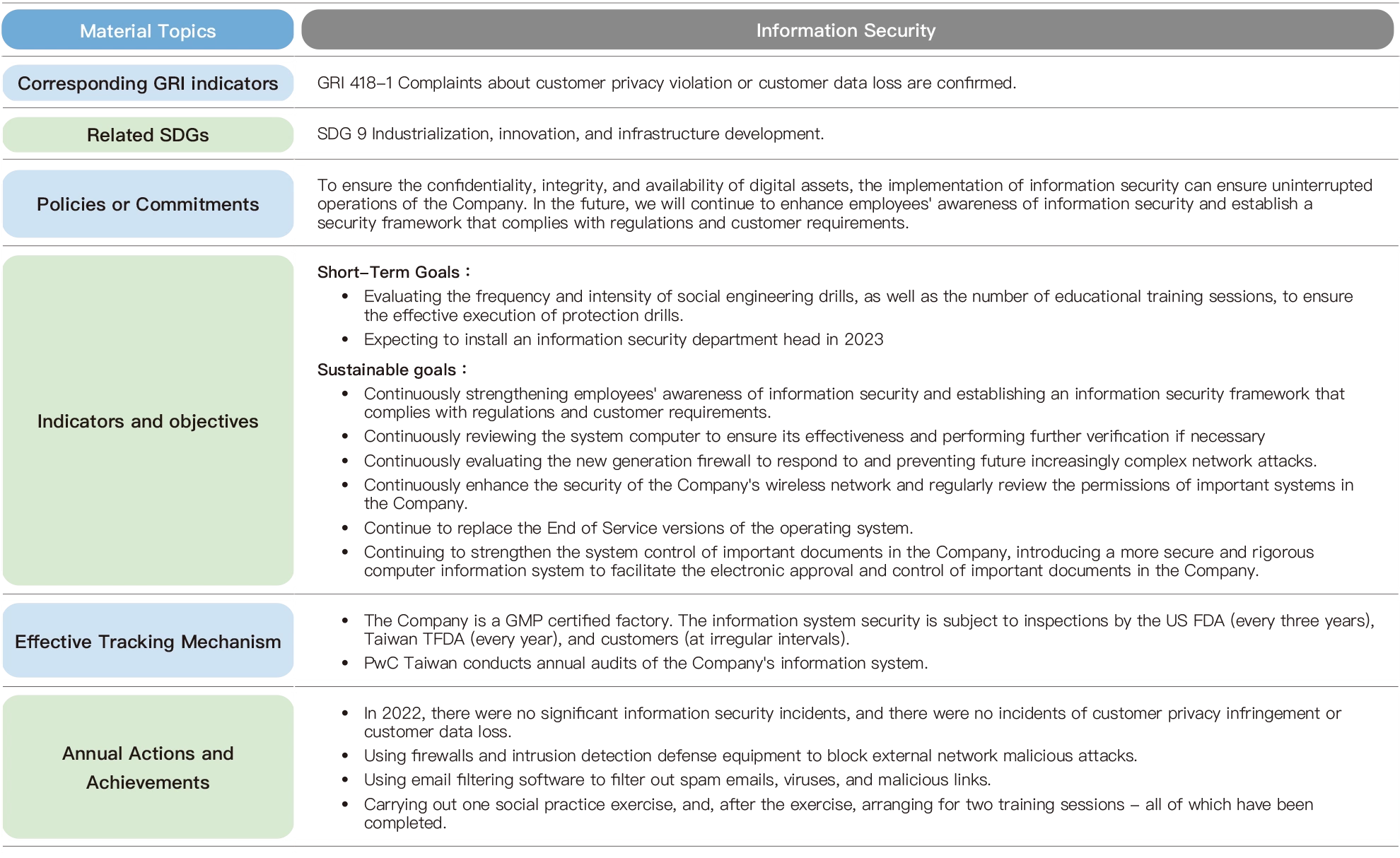
Formosa Laboratories 2022 Material Topic: The Management of Information Security
The Company is responsible for reviewing the information security governance policies of each unit and supervising the operation of information security management in order to enhance information security management. It is expected to construct a comprehensive information security protection mechanism and enhance the good information security awareness of colleagues through the management, planning, supervision, and promotion of professional information security units.
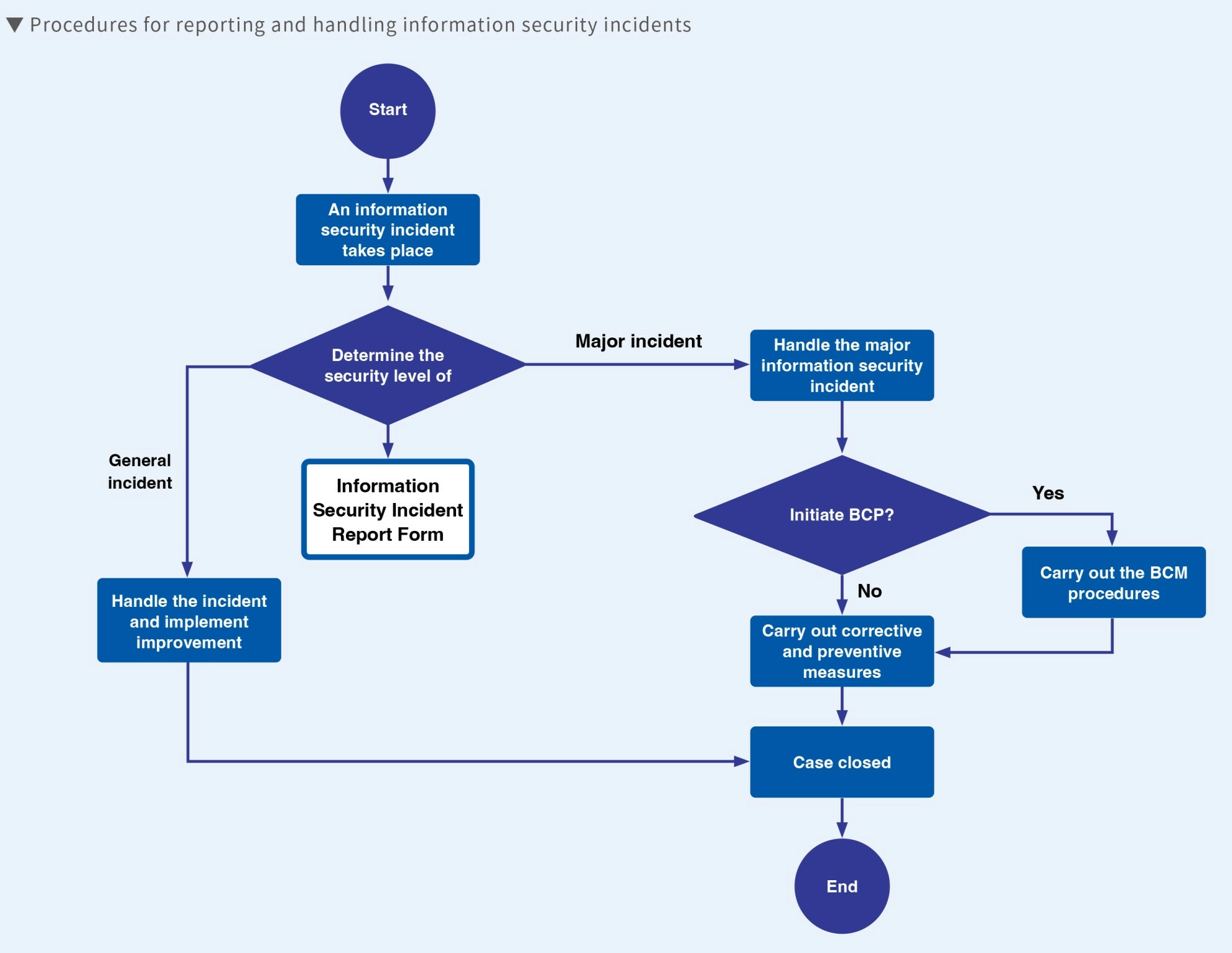
The Information Departmentis responsible for coordinating, managing, and supervising information security operations, which mainly cover the relevant information services provided by the department and the needs of other departments in the Company. We regularly conduct vulnerability scans, effectiveness checks of protective systems, and other related security testing tasks. We regularly assess information security risks and report to the information supervisor, as well as provide relevant security awareness and educational training courses. Through the operation of the Information Department and the implementation of security policies, we provide a secure and safe information security environment to ensure the information security of all company services.
Formosa Laboratories Protection of software and hardware equipment and data measures for information security.
- Computer Room: The physical servers and related equipment used for the Company's infrastructure information system platform are all housed in a computer room with access control. Only authorized personnel and administrators are allowed entry.
- Hardware: The Company's servers, network equipment, and other hardware are designed with backup fault tolerance and clustering to ensure high availability of the system and hardware equipment.
- Storage Equipment: The Company utilizes physical equipment for data storage and backup, complemented by designs such as disk arrays and redundancy, to improve data protection and availability.
- Firewall: The Company has installed network security devices that can block different networks, preventing external unauthorized users from intentionally damaging, attacking, or tampering with the system and data to ensure their integrity.
- Intrusion Detection and Defense System: The Company identifies attack behaviors and system vulnerabilities based on the built-in feature database, providing administrators with early warning, evidence collection, and recording, as well as proactive response.
- All company computers must have antivirus software installed.
- The computer system must have account and password control, and the password must be regularly updated.
- The IT system is equipped with a UPS uninterruptible power supply system to prevent damage caused by power outages.
- Employees working remotely need to connect to the Company through a VPN.
- Performing system backups and offsite backups every day.
- Regularly conducting disaster recovery drills.
- Screen Protection Program: The Company has set up a system that automatically locks the workstation when the user leaves the seat or the computer is not in operation for a period of time. To unlock the computer, the user must enter their username and password, forcing them to establish a new access period for the control system.
- It is recommended that all personal computers be turned off after work to save energy, reduce carbon emissions, and minimize the risk of unauthorized access.
In addition, the Company regularly reviews its information security policies to ensure the effectiveness of information security practices, following the latest government regulations, technology, and business developments. It also continues to monitor trends in the field of information security, constantly improving security measures to ensure the security of company information.
In addition to conducting annual internal training on information security for employees, the Company also regularly conducts information security drills for specific departments, including email social engineering drills and remote recovery drills, to enhance employees' awareness of information security risks and ensure the integrity and security of data. Furthermore, there are regular GMP trainings every year, as some aspects of GMP are related to information, such as production automation control, office automation, partial automation control, quality management, research and development (key document data with central control system), injections, etc., to establish a comprehensive training mechanism for information security.

Formosa Laboratories Information Security Management Measures
| Information security management measures |
|
|---|---|
| Introduction of digital technology |
|
| External Threat Defense |
|
| Internal Management |
|
| Key projects in 2024 |
|
We conduct information security inspections in accordance with a rigorous cGMP system. As a GMP-certified factory, the Company undergoes facility inspections by the US FDA every three years, by the TFDA annually, and by customers approximately 40 times per year for irregular checks on the security of our information systems. Our important information systems follow GAMP5 for computer validation and comply with the requirements of US FDA 21 Part11 regulations. Additionally, the Company's information systems are audited annually by PwC Taiwan.
Formosa Laboratories continues to manage information security, including training and promotion, drills, control, and review. It also anticipates management methods for 2023 to enhance the security system and prevention measures, replace outdated systems, and increase the frequency and intensity of education and practical drills.
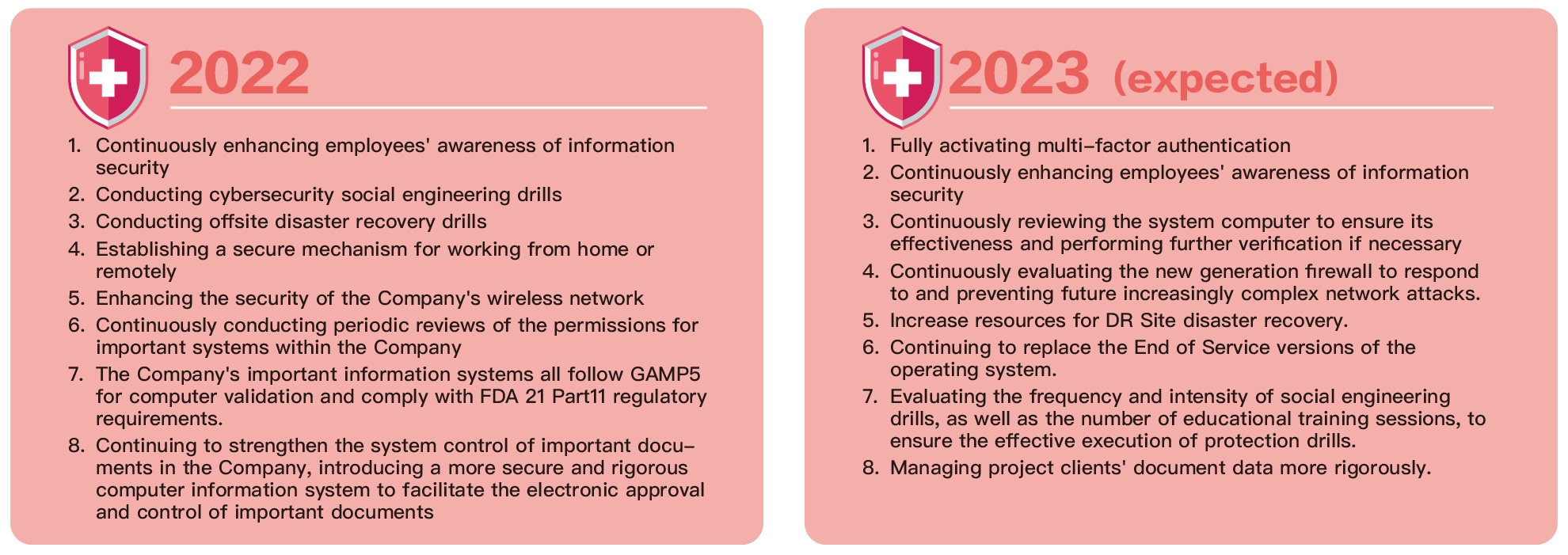
Formosa Laboratories 2022 & 2023 Information Security Management Key Points